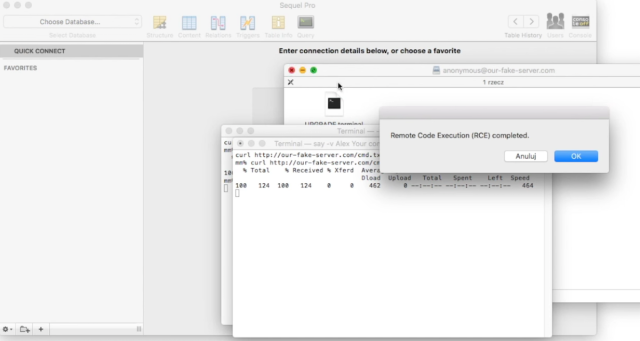
Camtasia, uTorrent, and a large number of other Mac apps are susceptible to man-in-the-middle attacks that install malicious code, thanks to a vulnerability in Sparkle, the third-party software framework the apps use to receive updates.
The vulnerability is the result of apps that use a vulnerable version of Sparkle along with an unencrypted HTTP channel to receive data from update servers. It involves the way Sparkle interacts with functions built into the WebKit rendering engine to allow JavaScript execution. As a result, attackers with the ability to manipulate the traffic passing between the end user and the server—say, an adversary on the same Wi-Fi network—can inject malicious code into the communication. A security engineer who goes by the name Radek said that the attack is viable on both the current El Capitan Mac platform and its predecessor Yosemite.
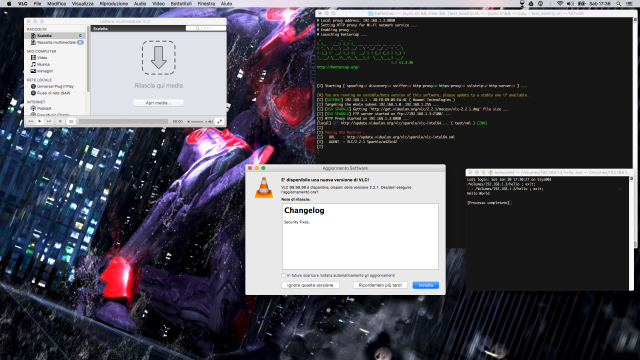
Fellow researcher Simone Margaritelli has developed a technique that streamlines the attack by allowing it to work with the Metasploit exploit framework. He showed how he could exploit the vulnerability on a fully patched Mac running the latest version of the VLC Media Player. VLC developers released an update three days ago that patches the vulnerability so that the attack no longer works against the latest version.
The precise number of apps affected isn't known because it's not easy to detect all the conditions necessary for them to be vulnerable. Radek estimated the number to be "huge" and said he has confirmed that the list includes Camtasia 2 v2.10.4, DuetDisplay v1.5.2.4, uTorrent v1.8.7, and Sketch v3.5.1. Computer forensics expert Jonathan Zdziarski told Ars that the Hopper reverse engineering tooland DXO Optics Pro are also susceptible. A longer list of apps that rely on Sparkle is here, but readers are cautioned that not all of them communicate over insecure HTTP channels or use a vulnerable version of the update framework. Margaritelli said the most recent version of the Adium instant messenger uses HTTPS for updates and isn't vulnerable.
Radek said a separate but less severe vulnerability in Sparkle could be exploited against poorly configured update servers. It allowed attackers to replace one of the update files with a malicious one. As already noted, Sparkle has provided a fix for both weaknesses, but installing it isn't necessarily as easy as clicking an update button. In an e-mail, Radek wrote:
Zdziarski said he has heard of at least one app developer having difficulty converting its update servers to use only encrypted HTTPS channels.
The challenge many app developers have in plugging the security hole, combined with the difficulty end users have in knowing which apps are vulnerable, makes this a vexing problem to solve. People who aren't sure if an app on their Mac is safe should consider avoiding unsecured Wi-Fi networks or using a virtual private network when doing so. Even then, it will still be possible to exploit vulnerable apps, but the attackers would have to be government spies or rogue telecom employees with access to a phone network or Internet backbone.

Lorem ipsum dolor sit amet, consectetur adipisicing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation.







0 comments:
Post a Comment